PRL Website and it’s security
- Category: Web Server Administration
About PRL Website
PRL Website has been developed using open source technologies like PHP, Drupal and MySQL. The web server has been hosted on the PRL premise. It is running Apache on Linux based distribution. Being Web Admin of the PRL website, my primary role is to monitor website and server security and to protect it from the Internet threats. I regularly monitor server logs and block any suspicious activity happening on the PRL website. We have redesigned the PRL website in 2016 and 2019 using Drupal Framework. I introduced the QR Code for the PRL website and personal details of an individual employee so that QR code can be used in various newsletter, annual report and individual visitor cards. As a member of the Website Improvisation Committee, we are also maintining social media accounts of PRL. I have also procured and configured wildcard SSL certificate i.e *.prl.res.in for PRL website and other services.
External and Internal security audit of PRL website
There are recruitment and conference related web application available on the PRL website. PRL users also host their dedicated web pages on the PRL website. We perform VAPT of such web content on staging environment before pushing it on to the production PRL website. To secure the PRL website, I have implemented open-source Web Application Firewall on the PRL web server. I have also configured protection from Denial-of-Service attacks for the PRL website. The system also automatically monitor logs and send alerts on email immediately. As per ISRO guidelines, all centres/units have to perform an external audit of the main website. PRL website had undergone a security audit by CDAC-Hyderabad. For which, I prepared a staging server (clone of PRL web-server) and fixed any vulnerability reported by CDAC.
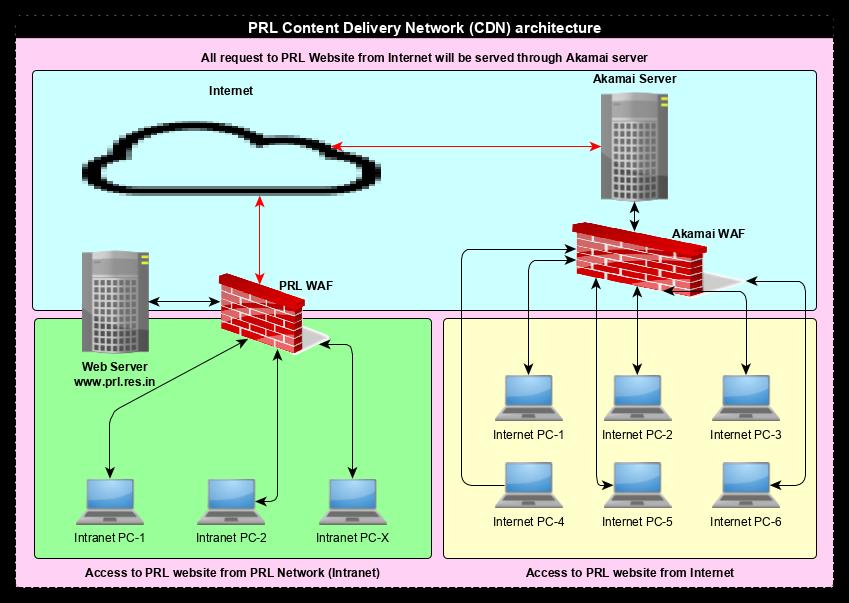
PRL Website on CDN
We moved the PRL website on the Content Delivery Network (CDN) in 2019. The CDN not only provides security to the website but also gives faster access to the website across the globe. It reduces the bandwidth load on PRL web-server by caching images, PDFs, media content, etc. The following diagram shows PRL’s CDN implementation architecture.
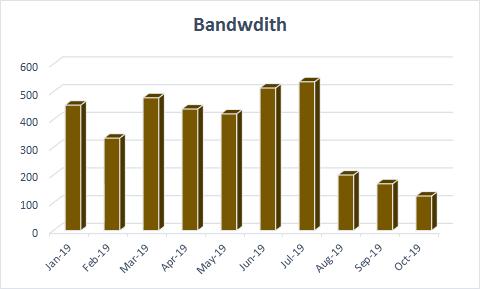
We moved the PRL website on CDN on 7th August 2019. The benefit of bandwidth (in GB) usage on the PRL website is clearly visible in Figure (b). CDN uses its own state-of-the-art Web Application Firewall to protect the web content and the WAF rules are updated immediately whenever any Common Vulnerabilities and Exposures (CVE) are reported. The CDN WAF protects the PRL website from all the web attacks.
Following tables shows some of the major web attack happenned before moving to CDN (but blocked by PRL WAF) and after implementation of CDN.
| Type of Web Attack | Before CDN | After CDN |
|---|---|---|
| DoS Attack | 44 | 1 |
| SQL Injection | 1716 | 81 |
| Request Missing a User Agent Header | 240 | 74 |
| Method is not allowed by policy | 113 | 5 |
| Request Containing Content, but Missing Content-Type header | 37 | 0 |
| GET or HEAD Request with Body Content. | 31 | 0 |
| Possible Remote File Inclusion (RFI) Attack: Off-Domain Reference/Link | 9 | 1 |
| Request Indicates a Security Scanner Scanned the Site | 11 | 0 |
| Cross Site Scripting (XSS) | 5 | 3 |
Technically, after CDN there should not be any attack on PRL web server. But, the WAF running at CDN are too mature to understand the attack pattern. Whereas the WAF implemented at PRL is open-source and some time it may blocks pattern which is false positive.
